Best Access Control System Solutions for Enhanced Security Management
Access Control System: Complete Guide to Modern Security Solutions

Key Takeaways
- Access control systems regulate who can enter specific areas using electronic credentials, biometrics, or mobile devices instead of traditional keys
- Modern systems integrate with video surveillance, alarm systems, and visitor management for comprehensive security coverage
- Mobile access control adoption has grown significantly, with over 70% of employees now using smartphones for workplace access
- Cloud-based access control offers scalability and remote management capabilities compared to traditional on-premise solutions
- Proper implementation includes authentication factors, audit trails, and compliance with standards like FIPS 201 for federal facilities

The modern workplace has transformed dramatically, and so have security requirements. Traditional mechanical keys are rapidly becoming obsolete as organizations discover the limitations of physical key management. An access control system represents the evolution of facility security, offering electronic management of who can access specific areas within your building or property.
Unlike mechanical keys that can be copied or lost without detection, access control systems provide real-time monitoring, instant credential management, and detailed audit trails. These systems have become essential infrastructure for businesses ranging from small offices to large enterprise facilities managing thousands of employees across multiple sites.
This comprehensive guide explores everything you need to know about access control systems, from basic concepts to advanced implementation strategies. Whether you’re considering your first system or upgrading existing infrastructure, understanding these modern security solutions will help you make informed decisions that protect your facility while supporting operational efficiency.
What is an Access Control System?
An access control system is an electronic security solution that manages and monitors entry to buildings, rooms, or restricted areas. Instead of relying on traditional mechanical keys, these systems use digital credentials to authenticate users and grants access based on predetermined permissions.
The fundamental purpose of any access control system is to replace mechanical keys with more secure and manageable alternatives. When someone approaches a protected area, they present their access credentials to a reader. The system verifies their identity and determines whether they have permission to enter that specific area at the current time.
Modern access control systems provide several critical functions that traditional keys cannot match:
Authentication and Authorization: The system verifies user identity through access control credentials such as cards, key fobs, biometric data, or mobile devices. It then checks whether that person has permission to access the requested area.
Real-time Monitoring: Unlike mechanical keys, access control systems create detailed logs of every entry attempt. System administrators can monitor who accessed which areas and when, providing complete situational awareness of facility activity.
Instant Credential Management: When an employee leaves or a credential is compromised, access can be immediately revoked without changing physical locks or redistributing keys to other users. This eliminates the time consuming process of re-keying locks across your facility.
Integration Capabilities: Most access control systems can integrate with other systems including video surveillance, alarm systems, and visitor management platforms. This creates a comprehensive security solution that protects your facility more effectively than standalone systems.
The technology behind these systems has evolved significantly in recent years. While early systems relied solely on physical credentials like magnetic stripe cards, today’s solutions support mobile credentials, facial recognition, and multi-factor authentication. This evolution has made access control systems more convenient for users while simultaneously improving security.
Types of Access Control Systems
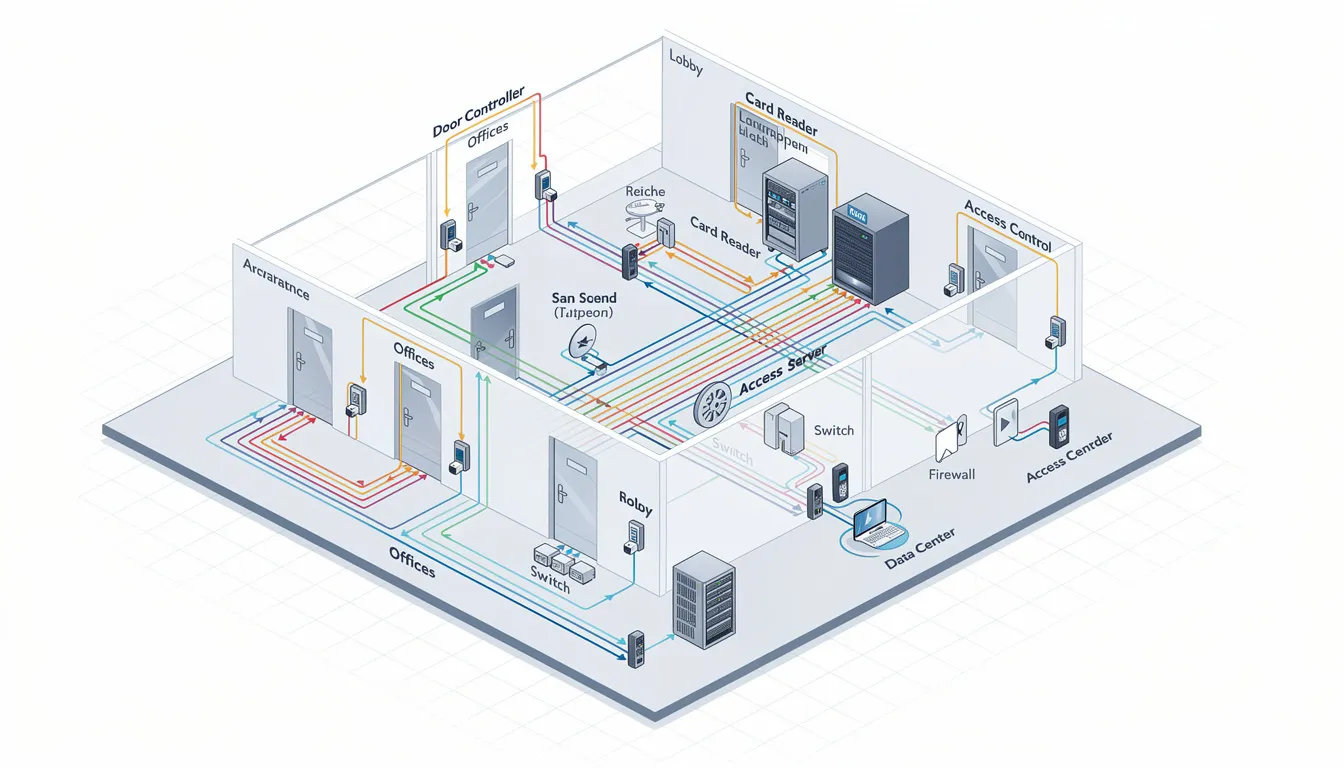
Understanding the different types of access control systems helps you choose the right solution for your specific needs. Each type offers distinct advantages depending on your facility size, security requirements, and budget considerations.
Standalone Access Control Systems
Standalone access control systems represent the simplest deployment model, designed to control access to individual doors or small areas without requiring network connectivity. These self-contained units include the control system, reader, and locking hardware in a single integrated solution.
The primary advantage of standalone systems is their simplicity. No software installation or network infrastructure is required, making them ideal for small businesses or organizations with basic security needs. Each unit operates independently, storing user credentials locally and making access decisions without communicating with other systems.
Common applications for standalone systems include single-door offices, storage rooms, or isolated high-security areas like SCIFs (Sensitive Compartmented Information Facilities) where network connectivity might create security concerns. These systems often cost less initially but become expensive to manage as you add more doors or users.
The main limitation of standalone systems is their lack of centralized management. Each door must be programmed individually, and adding or removing users requires physical access to each control panel. This becomes time consuming and impractical for facilities with multiple access points or frequent credential changes.
Networked Access Control Systems
Networked access control systems connect multiple door controllers through your facility’s network infrastructure, enabling centralized management from a single software platform. This architecture supports hundreds or thousands of doors while maintaining real-time communication between all components.
The key benefit of networked systems is their scalability and management efficiency. System administrators can add new users, modify access permissions, and monitor activity across the entire facility from one centralized location. When someone’s access needs to change, updates are instantly distributed to all relevant access points throughout your network.
These systems excel at integration with existing systems like video surveillance, alarm systems, and visitor management platforms. When an access event occurs, the system can automatically trigger cameras to record the entry, send notifications to security personnel, or activate other security measures based on predefined rules.
Networked access control solutions provide detailed reporting capabilities that help organizations meet compliance requirements and conduct security audits. The software can generate reports showing who accessed specific areas, unusual access patterns, or attempted unauthorized entries.
The primary consideration for networked systems is their dependence on network infrastructure. Proper network design and redundancy become critical to ensure reliable operation. However, most modern systems include local intelligence that allows doors to continue operating even if network connectivity is temporarily lost.
Cloud-Based Access Control
Cloud-based access control represents the newest evolution in access control technology, moving system management and data storage to remote servers hosted by the access control provider. This software-as-a-service model eliminates the need for on-site servers while providing advanced functionality and automatic updates.
The most significant advantage of cloud-based systems is their accessibility. Authorized personnel can manage the system from anywhere with internet access, making them ideal for organizations with multiple sites or remote management needs. This capability proved especially valuable during the pandemic when facility managers needed to manage access while working from home.
Cloud-based solutions typically offer lower upfront costs since they eliminate server hardware and reduce IT infrastructure requirements. The subscription pricing model spreads costs over time and includes automatic software updates, technical support, and system maintenance that would otherwise require internal resources.
These systems provide excellent scalability for growing organizations. Adding new doors or locations requires minimal additional infrastructure, and the cloud platform can accommodate expansion without significant hardware investments. This flexibility makes cloud-based access control particularly attractive for multi-site organizations or rapidly growing businesses.
Security concerns about cloud-based systems have largely been addressed through enterprise-grade encryption, multi-factor authentication for system access, and compliance with security standards. Most cloud providers offer better security and redundancy than typical on-premise installations, with professional monitoring and backup capabilities that smaller organizations couldn’t afford to implement internally.
Key Components and Technology

Understanding the components that make up an access control system helps you make informed decisions about technology choices and system design. Modern systems combine various hardware and software elements to create comprehensive security solutions.
Credential Technologies
The evolution of access credentials represents one of the most significant advances in access control technology. While traditional mechanical keys provided basic security, modern credential technologies offer enhanced security, convenience, and management capabilities.
Proximity Cards and Key Fobs: Most access control systems support proximity cards using 125 kHz technology for basic access control applications. These cards contain embedded antennas that communicate with readers when brought within range. Key fobs offer the same functionality in a more convenient form factor that users can attach to keychains.
Smart Cards: Advanced installations often use smart cards with embedded microprocessors and encrypted data storage. These cards can store multiple applications, support stronger encryption, and provide enhanced security for high-risk environments. Common examples include PIV cards for federal facilities and corporate ID cards with embedded access credentials.
Mobile Credentials: The fastest-growing segment of access control technology uses smartphones as credentials. Mobile access control leverages technologies like NFC, Bluetooth Low Energy, or QR codes to communicate with readers. Users simply present their phone to the reader, often with additional authentication through the device’s biometric features.
Biometric Authentication: Advanced systems incorporate biometric readers that authenticate users based on unique physical characteristics. Fingerprint readers remain the most common biometric technology, but facial recognition systems are gaining popularity. Iris scanning provides the highest security level but requires specialized hardware.
Multi-Factor Authentication: High-security applications often combine multiple credential types for enhanced protection. Common combinations include cards plus PIN codes, or mobile credentials with biometric verification. This approach significantly reduces the risk of unauthorized access even if one factor is compromised.
Hardware Components
The physical components of an access control system work together to authenticate users and control physical barriers. Understanding these components helps you design systems that meet your security requirements while providing reliable operation.
Card Readers and Biometric Devices: These devices capture credential information and communicate with the control system. Proximity card readers use radio frequency communication, while smart card readers establish direct contact with the card’s microprocessor. Biometric devices include fingerprint scanners, facial recognition cameras, and iris readers.
Control Panels and Door Controllers: The “brain” of each access point, these devices process authentication requests and make access decisions. Modern door controllers include local intelligence that can operate independently if network connectivity is lost. They connect to readers, locking hardware, and other devices at each access point.
Electric Locking Hardware: Access control systems use various types of electric locks to secure doors. Electric strikes modify existing door frames to work with electronic control. Magnetic locks create powerful electromagnetic bonds between door and frame. Motorized locks provide both electronic and mechanical security with battery backup operation.
Request-to-Exit Devices: These devices detect when authorized users want to leave secured areas. Motion sensors automatically detect approaching users and unlock doors for egress. Exit buttons provide manual request capability. Door position sensors monitor whether doors are properly closed and locked.
Power Supplies and Backup Systems: Reliable power is critical for access control operation. Uninterruptible power supplies provide battery backup during power outages. Some systems include sufficient backup power to operate for hours during extended outages, ensuring security is maintained even during emergencies.
Software and Management
The software component of access control systems provides the interface for managing users, monitoring activity, and generating reports. Modern access control software has evolved into sophisticated platforms that support complex security policies and integrate with multiple other systems.
User Management: Access control software enables administrators to create user profiles, assign access credentials, and define permissions for specific areas and time periods. Advanced systems support role-based access control that automatically assigns permissions based on job title or department membership.
Real-Time Monitoring: The software provides live views of access activity throughout your facility. Administrators can see who is currently in secured areas, receive alerts about unusual activity, and respond to access attempts in real-time. This capability supports both security and emergency response procedures.
Reporting and Audit Trails: Comprehensive reporting capabilities help organizations meet compliance requirements and conduct security investigations. The software can generate detailed logs of all access activity, create exception reports for unusual events, and provide analytics on facility usage patterns.
Integration Capabilities: Modern access control software includes APIs and integration tools that connect with HR systems, visitor management platforms, video surveillance systems, and alarm systems. These integrations automate user provisioning, enhance security response, and provide comprehensive facility management capabilities.
Mobile Management Apps: Many systems include mobile applications that allow administrators to manage access permissions remotely, grant temporary access to visitors, and monitor system status from smartphones or tablets. This capability is particularly valuable for after-hours management and emergency response situations.
Benefits of Modern Access Control Systems

Implementing an access control system provides measurable benefits that extend beyond basic security improvements. Organizations consistently report significant operational efficiencies, cost savings, and enhanced security posture after replacing traditional lock-and-key systems.
Enhanced Security and Control
The security advantages of access control systems become apparent immediately after implementation. Unlike mechanical keys that provide no accountability, electronic access control creates detailed records of every entry attempt and provides precise control over who can access specific resources.
Elimination of Key-Related Security Risks: Traditional mechanical keys present numerous security vulnerabilities that access control systems eliminate entirely. Lost or stolen keys cannot be easily tracked or controlled, potentially compromising security for extended periods. Access cards can be instantly deactivated the moment they’re reported missing, preventing any unauthorized use.
Time-Based Access Restrictions: Access control systems enable precise control over when people can enter specific areas. Employees might have 24/7 access to general office areas but restricted access to server rooms only during business hours. Contractors might receive access only during their project timeline, automatically expiring when work is completed.
Anti-Tailgating and Area Control: Advanced systems include features that prevent unauthorized entry behind authorized users. Turnstiles, mantraps, and intelligent monitoring systems can detect when multiple people attempt to enter on a single credential presentation. Integration with video surveillance provides visual verification of access events.
Integration with Security Systems: When access control systems integrate with video surveillance and alarm systems, they create comprehensive security coverage. Cameras can automatically record access events, and alarms can trigger if doors are forced open or remain open too long. This integration provides both deterrent effects and forensic capabilities for security incidents.
Emergency Response Capabilities: During emergencies, access control systems can instantly unlock all doors for evacuation while maintaining detailed records of who was in which areas. This information proves invaluable for emergency responders and helps ensure all personnel are safely evacuated.
Operational Efficiency
Beyond security improvements, access control systems significantly streamline facility management operations and reduce administrative overhead associated with traditional key management.
Simplified Credential Management: Adding new employees to an access control system takes minutes compared to the time consuming process of key duplication and distribution. When employees change roles or departments, their access can be updated instantly without collecting and redistributing physical keys. This efficiency becomes particularly valuable for organizations with high employee turnover.
Reduced Employee Access Complaints: Studies show a 98% reduction in employee complaints about restrictive access compared to traditional key systems. Employees appreciate the convenience of carrying a single credential that works across multiple areas, and the reliability of electronic systems eliminates frustration with mechanical lock failures.
Automated Visitor Management: Integration with visitor management systems enables temporary access credentials for guests, contractors, and vendors. Visitors can receive temporary cards or mobile credentials that automatically expire, eliminating the need to track and collect visitor badges. Some systems even allow pre-registration so visitors can proceed directly to their destination.
Remote Access Management: Cloud-based and networked systems allow facility managers to grant emergency access remotely without traveling to the facility. This capability proves essential for after-hours vendor access, emergency maintenance, and supporting employees who need temporary access to restricted areas.
Detailed Activity Reporting: The audit trails generated by access control systems provide valuable insights into facility usage patterns. Organizations can identify underutilized areas, optimize space allocation, and understand peak usage times for better resource planning.
Cost Savings
While access control systems require initial investment, they typically generate significant cost savings through reduced security incidents, lower administrative overhead, and elimination of key-related expenses.
Elimination of Re-keying Costs: Traditional lock systems require expensive re-keying whenever keys are lost or stolen, or when employee access needs change. A single re-keying event can cost hundreds or thousands of dollars depending on facility size. Access control systems eliminate these costs entirely through electronic credential management.
Reduced Security Personnel Requirements: Automated access control reduces the need for security guards at building entrances and internal checkpoints. The system provides the same access verification and logging functions without ongoing personnel costs. For larger facilities, this can represent substantial savings in security staffing costs.
Lower Insurance Premiums: Many insurance companies offer reduced premiums for facilities with electronic access control systems. The improved security, detailed audit trails, and integration with other security systems demonstrate reduced risk that insurers recognize through lower rates.
Decreased Facility Management Costs: Integration with other building systems enables centralized management that reduces overall facility management costs. HVAC systems can be programmed to operate only in occupied areas, and lighting systems can automatically adjust based on access patterns.
Return on Investment: Most organizations achieve return on investment within 12-18 months for medium to large installations. The combination of operational efficiencies, reduced security incidents, and eliminated key management costs quickly offset the initial system investment.
Implementation and Deployment Considerations

Successful access control system implementation requires careful planning, professional installation, and ongoing management to ensure optimal security and reliability. Understanding the implementation process helps organizations avoid common pitfalls and achieve their security objectives.
System Planning and Design
Effective access control system design begins with a comprehensive assessment of your facility’s security requirements, user populations, and integration needs. This planning phase determines system architecture and technology choices that will serve your organization for years.
Facility Security Assessment: Professional security consultants evaluate your facility to identify critical assets, potential vulnerabilities, and appropriate security levels for different areas. This assessment considers factors like the sensitivity of information or materials in each area, employee populations, visitor requirements, and compliance obligations.
User Population Analysis: Understanding your current and future user populations helps determine appropriate credential technologies and system capacity. Consider not only current employees but also contractors, visitors, vendors, and temporary workers who may need access. Plan for growth to avoid costly system expansions in the near future.
Integration Requirements: Evaluate existing security and IT infrastructure to identify integration opportunities and requirements. Consider connections with video surveillance systems, alarm systems, visitor management platforms, HR databases, and building automation systems. These integrations often provide the greatest value from access control investments.
Scalability Planning: Design systems with future expansion in mind. Consider potential facility growth, additional doors, increased user populations, and new technology adoption. Cloud-based systems often provide better scalability than on-premise solutions, but network infrastructure requirements must be carefully planned.
Network Infrastructure Evaluation: Networked access control systems depend on reliable network connectivity between door controllers and management systems. Evaluate existing network infrastructure for adequate bandwidth, power over Ethernet capabilities, and redundancy requirements. Plan for backup power and network failover to ensure continued operation during outages.
Installation and Configuration
Professional installation by qualified technicians ensures proper system operation and optimal security. The installation process involves both physical hardware installation and software configuration that must be carefully coordinated.
Professional Installation Requirements: Access control systems include both low-voltage electronics and mechanical hardware that require specialized installation skills. Certified technicians understand proper wire routing, power requirements, and mechanical integration that ensure reliable long-term operation. Many manufacturers require certified installation to maintain warranty coverage.
Network Configuration: Proper network configuration ensures reliable communication between system components and integration with existing IT infrastructure. This includes IP addressing, VLAN configuration, firewall settings, and Quality of Service parameters that prioritize access control traffic.
User Enrollment and Credential Provisioning: Initial user enrollment involves collecting user information, creating system profiles, and assigning appropriate access permissions. For biometric systems, this includes capturing fingerprints or facial recognition templates. Plan adequate time for user enrollment, especially for large organizations.
System Testing and Validation: Comprehensive testing verifies that all access points function correctly and that access permissions are properly configured. Test emergency procedures, backup power systems, and integration with other security systems. Document any issues and ensure they’re resolved before system acceptance.
Staff Training: Proper training for system administrators and end users ensures effective system operation. Administrators need training on user management, monitoring procedures, and basic troubleshooting. End users need orientation on proper credential use and emergency procedures.
Ongoing Management
Access control systems require ongoing attention to maintain security effectiveness and optimal operation. Regular maintenance, user access reviews, and system updates keep the system functioning reliably and securely.
Regular System Maintenance: Preventive maintenance includes cleaning readers, testing backup power systems, updating software, and replacing batteries in door controllers. Establish maintenance schedules that prevent failures and extend equipment life. Many organizations contract with professional service providers for ongoing maintenance.
User Access Reviews: Regular reviews of user access permissions ensure that employees have appropriate access for their current roles and that former employees or contractors are properly removed from the system. Many organizations conduct quarterly access reviews to maintain security and compliance.
Backup and Disaster Recovery: Implement backup procedures for system databases and configuration files. For cloud-based systems, verify backup and recovery procedures with your service provider. Test disaster recovery procedures periodically to ensure you can restore system operation after equipment failures.
Performance Monitoring: Monitor system performance to identify potential issues before they cause failures. This includes network connectivity, door controller status, and reader performance. Many systems provide automated health monitoring and alerting capabilities.
Compliance Documentation: Maintain documentation required for security audits and compliance requirements. This includes access logs, system configuration records, maintenance logs, and user access reviews. Proper documentation demonstrates due diligence in security management.
Security and Compliance
Access control systems often operate in regulated environments where specific security standards and compliance requirements must be met. Understanding these requirements ensures your system design and implementation meet both security objectives and regulatory obligations.
Federal and Industry Standards
Government and industry organizations have developed comprehensive standards that define security requirements for access control systems in various environments. These standards provide frameworks for secure implementation and operation.
FIPS 201-3 Compliance: Federal facilities and contractors must comply with FIPS 201-3 standards that define requirements for Personal Identity Verification (PIV) credentials. These standards specify cryptographic requirements, physical security features, and lifecycle management for access credentials used in federal facilities.
NIST Guidelines: The National Institute of Standards and Technology provides comprehensive guidance for physical access control systems through publications like NIST SP 800-116. These guidelines address system architecture, security controls, and operational procedures for facilities handling sensitive information.
GSA Approved Products List: Government installations must use products from the GSA Approved Products List (APL) that have undergone security evaluation and certification. This requirement ensures that government facilities use access control solutions that meet federal security standards.
Industry Certifications: Professional certifications like the Certified Security Electronics Installation Professional (CSEIP) program ensure that system designers and installers understand proper security implementation practices. These certifications demonstrate competency in access control system design and installation.
Security Best Practices
Implementing access control systems according to established security best practices helps organizations achieve optimal security while avoiding common vulnerabilities that could compromise system effectiveness.
Multi-Factor Authentication: High-security environments should implement multi-factor authentication that requires users to present multiple forms of identification. Common combinations include proximity cards plus PIN codes, or biometric authentication combined with traditional credentials. This approach significantly reduces the risk of unauthorized access even if credentials are compromised.
Principle of Least Privilege: Access control policies should grant users the minimum access required for their job functions. Regular reviews ensure that access permissions remain appropriate as job roles change. Temporary access for contractors and visitors should automatically expire to prevent long-term unauthorized access.
Encryption and Secure Communications: All communications between system components should use strong encryption to prevent interception and tampering. This includes communications between readers and controllers, and between controllers and management systems. Mobile credentials should use encrypted protocols that prevent cloning or replay attacks.
Regular Security Assessments: Periodic security assessments evaluate system vulnerabilities and verify that security controls remain effective. These assessments should include both physical security testing and cybersecurity evaluation of system networks and software components.
Incident Response Procedures: Develop and maintain procedures for responding to security incidents involving access control systems. This includes procedures for responding to forced entry, credential compromise, system tampering, and other security events. Regular training ensures that security personnel can respond effectively to incidents.
Privacy and Data Protection
Access control systems collect and store sensitive personal information that requires appropriate protection to comply with privacy regulations and maintain user trust.
Biometric Data Protection: Biometric systems collect highly sensitive personal data that requires special protection. Best practices include storing biometric templates rather than actual biometric images, encrypting all biometric data, and implementing secure deletion procedures when users leave the organization.
Data Retention Policies: Establish clear policies for how long access logs and user data are retained. Consider legal requirements, operational needs, and privacy principles when setting retention periods. Implement automated deletion procedures to ensure data is not retained longer than necessary.
User Consent and Notification: Collect appropriate consent from users before enrolling biometric data or implementing tracking capabilities. Provide clear notification about what data is collected, how it’s used, and how long it’s retained. Respect user privacy rights and provide mechanisms for users to request data deletion.
GDPR Compliance: Organizations operating in Europe or handling EU citizen data must comply with General Data Protection Regulation requirements. This includes obtaining proper consent, implementing data protection by design, providing data subject rights, and ensuring appropriate security measures for personal data.
Access Logging and Monitoring: While access control systems necessarily log user activity, implement policies that balance security monitoring with employee privacy. Avoid excessive surveillance and ensure that access logs are used only for legitimate security and operational purposes.
Frequently Asked Questions
What is the difference between access control and traditional lock and key systems?
Access control systems provide electronic authentication, detailed audit trails, and remote management capabilities that traditional mechanical keys cannot offer. Lost or stolen access cards can be instantly deactivated without changing locks or distributing new keys throughout your facility. Additionally, time-based restrictions and user-specific permissions are impossible with mechanical keys. Access control systems also integrate seamlessly with other security technologies like video surveillance and alarm systems, creating comprehensive security coverage that mechanical locks cannot provide.
How much does an access control system typically cost?
Costs vary significantly based on facility size, number of doors, system type, and integration requirements. Standalone single-door systems start around $500-1,500 per door including hardware and installation. Enterprise networked systems range from $1,000-5,000 per door depending on features and integration complexity. Cloud-based systems often use subscription pricing of $50-200 per door per year plus initial hardware costs. When calculating total cost of ownership, include ongoing maintenance, support, credential replacement expenses, and potential savings from eliminated re-keying costs and reduced security staffing requirements.
Can access control systems work during power outages?
Most modern access control systems include battery backup capabilities providing 4-24 hours of operation during power failures. Magnetic locks typically fail-safe (unlock) during power loss for fire safety compliance, while electric strikes can be configured as fail-safe or fail-secure depending on security requirements. Uninterruptible Power Supply (UPS) systems can extend backup power duration for critical installations. Many systems store recent access decisions locally to continue operating even if network connectivity is lost, ensuring that authorized personnel maintain access during emergencies.
How secure are mobile access control credentials compared to physical cards?
Mobile credentials often provide enhanced security through built-in encryption, biometric authentication, and device-level security features. Smartphones typically require additional authentication like fingerprint or face recognition to access credential apps, adding an extra security layer. Remote wipe capabilities allow instant deactivation of mobile credentials on lost or stolen devices. Mobile credentials use secure communication protocols like encrypted Bluetooth Low Energy or NFC with cryptographic protection. However, proper implementation of security protocols and regular software updates are essential to maintain protection levels equivalent to or better than traditional physical credentials.
What happens if the access control system fails or needs maintenance?
Well-designed systems include redundancy and fail-over capabilities to minimize downtime during maintenance or failures. Local controllers can operate independently for short periods if the central server becomes unavailable, using cached credentials and access permissions. Emergency procedures should include mechanical key overrides for critical areas during system maintenance. Most systems provide 24/7 monitoring and technical support with guaranteed response times for critical issues. Regular preventive maintenance and system health monitoring help identify potential problems before they cause failures, ensuring maximum uptime and reliability for your security infrastructure.



